The most common way threat actors infiltrate cloud environments
techrepublic.com - cloud
Financially motivated threat actors are increasingly sabotaging cloud backups in addition to primary data, aiming to maximize leverage in extortion schemes, Google warned in its H2 2025 Cloud Threat Horizons Report, released today.
These threat actors may disable backup routines, delete stored data, or alter user permissions to block recovery attempts.
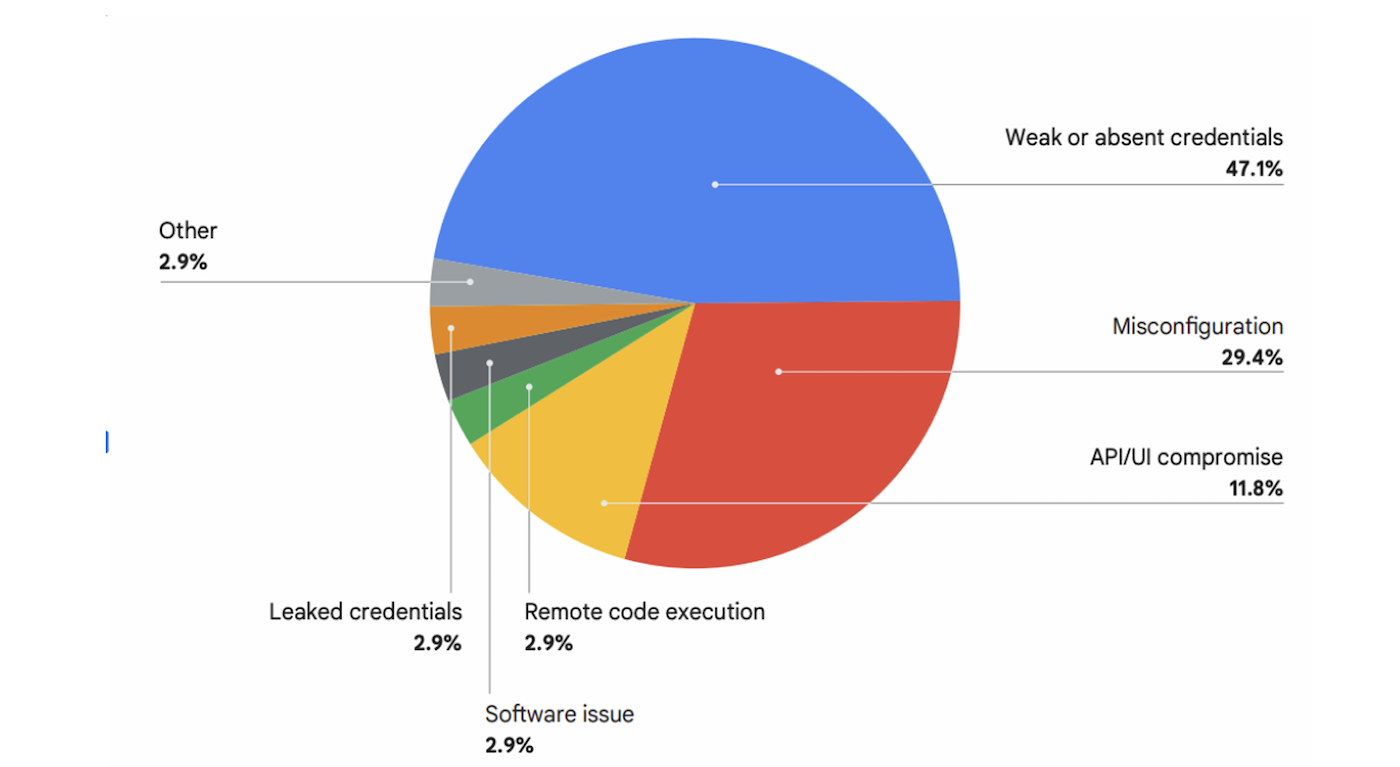
In the second half of 2025, credential compromise accounted for 47% of cloud security incidents, while misconfiguration followed at 29%, according to Google Cloud. Leaked credentials — present in 2.9% of initial access cases — also posed a growing concern.
The report noted that the sources of predominant threats were very similar to trends from earlier in the year. The most common access points were weak or absent credentials, misconfigurations, and API or UI compromises.
Copyright of this story solely belongs to techrepublic.com - cloud . To see the full text click HERE



