Researchers Turned Azure Storage Wildcards into a Stealthy Internal SOCKS5 Backdoor
gbhackersSecurity researchers at Quarkslab have developed a new covert channel technique that exploits Microsoft’s recommended Azure Storage firewall configurations to bypass network restrictions.
Their proof-of-concept tool, named “ProxyBlob,” leverages Azure Blob Storage to create a SOCKS5 proxy, allowing attackers to establish persistent backdoor access to restricted networks.
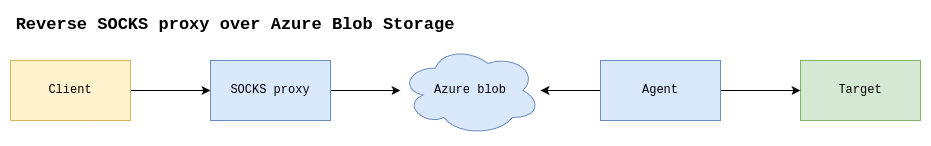
This technique demonstrates how Microsoft’s own security recommendations for allowing wildcard connections to Azure Blob Storage can be abused to maintain stealthy connections to compromised environments.
The Azure Storage Wildcard Vulnerability
During an assumed breach operation for a client, Quarkslab’s security team identified that while most external network connections were blocked, Microsoft services-particularly Azure Blob Storage-remained accessible through a wildcard allow rule.
The researchers discovered that jump boxes used for accessing internal services could reach any Azure Blob Storage container, despite stringent network restrictions.
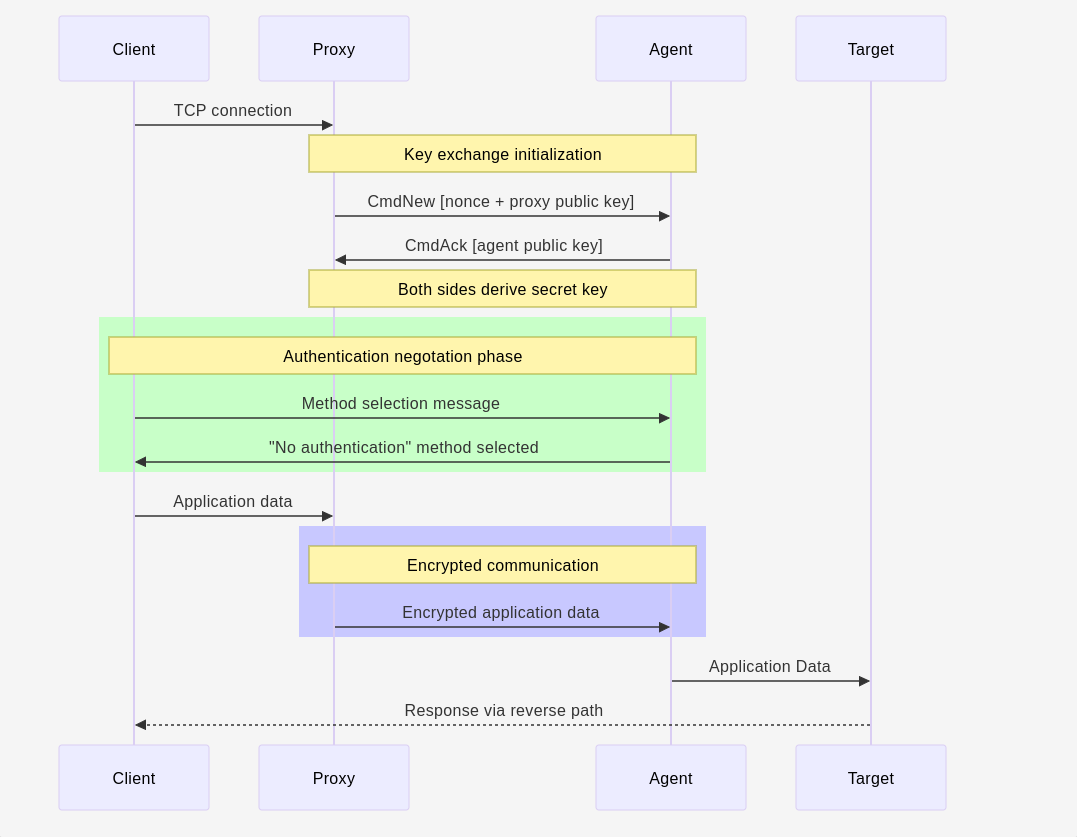
“We proved that even with restrictions in place, it ...
Copyright of this story solely belongs to gbhackers . To see the full text click HERE



