How to Secure Applications During Modernization on AWS
perficient.com
Cloud environments are very dynamic and interconnected. A single misconfiguration or exposed API key can lead to:
- Data breaches
- Compliance violations
- Costly downtime
Attackers often target application-level weaknesses, not just infrastructure gaps. If any application handles sensitive data, financial transactions, or user credentials, security is critical.
Common Mistakes Made When Building Applications
- Hardcoding API keys and credentials
- Ignoring dependency vulnerabilities
- Skipping encryption/decryption for sensitive data
Essential Security Best Practices
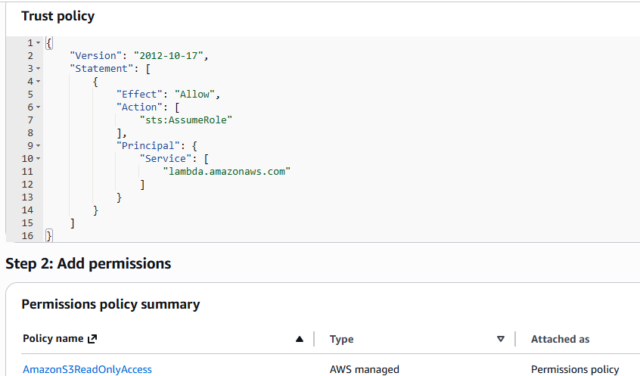
1. Identity and Access Management (IAM)
- Create dedicated IAM roles for your Lambda functions, EC2 instances, or ECS tasks instead of hardcoding access keys in your application.
- We must regularly review who has permissions using the IAM Access Analyzer.
- We must avoid using the root account for day-to-day operations/ any operations as a developer.
2. Don’t Store/Share Secrets in Your Code
Your appsettings.json is not the right place for secret keys. Storing API keys or database passwords ...
Copyright of this story solely belongs to perficient.com . To see the full text click HERE



