Advanced Serverless Security: Zero Trust Implementation with AI-Powered Threat Detection
hackread.comServerless architectures have fundamentally altered the cybersecurity landscape, creating attack vectors that traditional security models cannot address. After implementing serverless security for Fortune 500 companies that process over 10 billion API calls monthly, I have identified critical gaps in conventional approaches and developed advanced countermeasures that provide enterprise-grade protection against sophisticated threats, including function event injection, cold start exploitation, and AI-powered attacks.
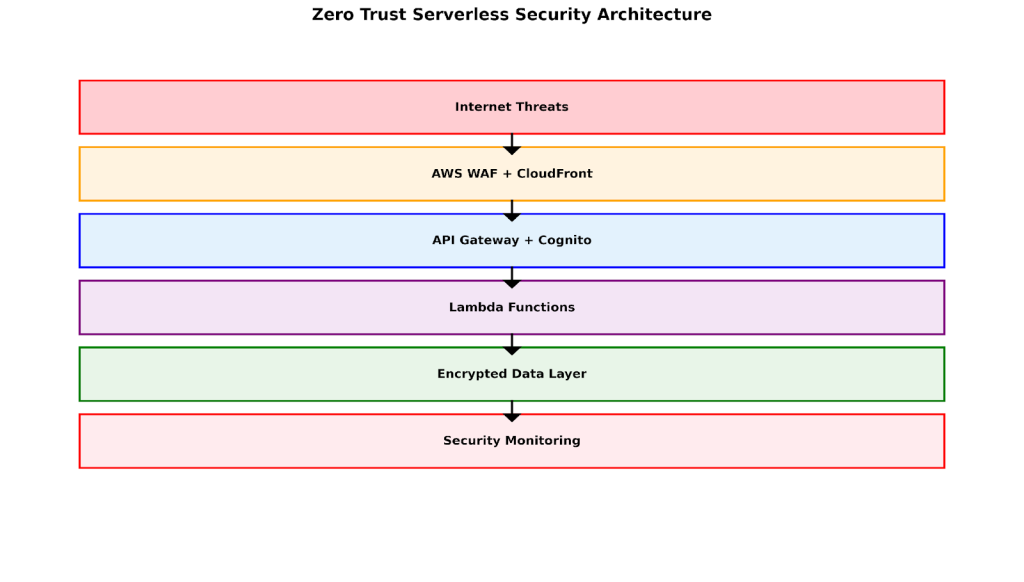
Zero Trust Serverless Architecture: Beyond Perimeter Security
Traditional perimeter-based security fails catastrophically in serverless environments due to the distributed, ephemeral nature of compute resources. Zero Trust implementation requires identity-centric verification for every function invocation, API call, and data access, regardless of source or previous authentication status.
The architecture implements defense-in-depth with six security layers: edge protection via AWS WAF, identity verification through Cognito advanced security features, function-level authorization, encrypted data access, and continuous monitoring. Each layer provides independent security controls that ...
Copyright of this story solely belongs to hackread.com . To see the full text click HERE