Zyxel RCE Flaw Lets Attackers Run Commands Without Authentication
gbhackersSecurity researcher Alessandro Sgreccia (aka “rainpwn”) has revealed a set of critical vulnerabilities in Zyxel’s USG FLEX-H firewall series that enable remote code execution (RCE) and privilege escalation—without authentication.
The findings, affecting models including the FLEX 100H and FLEX 700H, threaten the security of organizations relying on these devices for network defense.
How the Exploit Works
The root of the flaw lies in the misconfiguration of a third-party component: PostgreSQL. Although the database itself was up-to-date and secure, Zyxel’s implementation left it exposed to attack due to improper access controls:
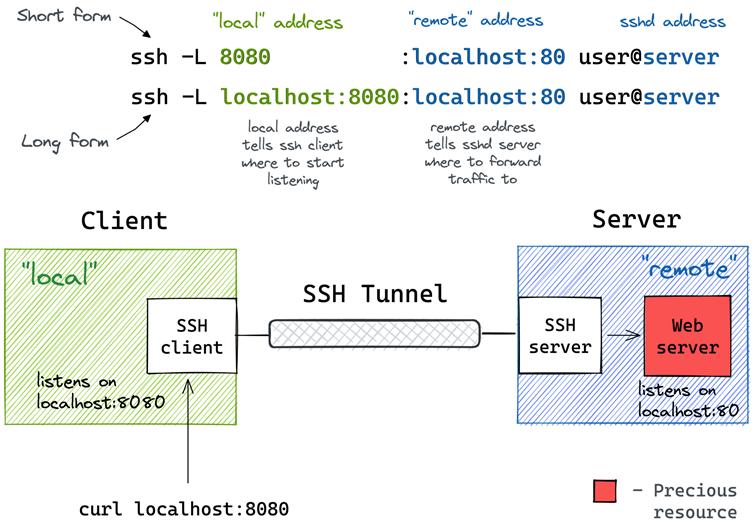
- PostgreSQL Service Exposure: The database runs on localhost:5432, theoretically shielded from remote attacks. However, if an attacker gains even momentary access (e.g., via a valid SSH session), they can establish an SSH tunnel to forward port 5432, exposing the database externally.
- No Authentication: Critically, the PostgreSQL instance was not password-protected ...
Copyright of this story solely belongs to gbhackers . To see the full text click HERE




.png)