New Malicious Rust Crates Impersonate fast_log to Steal Solana and Ethereum Wallet Keys
gbhackersA pair of malicious Rust crates masquerading as the popular fast_log library have been uncovered, harvesting private Solana and Ethereum keys from developers’ environments.
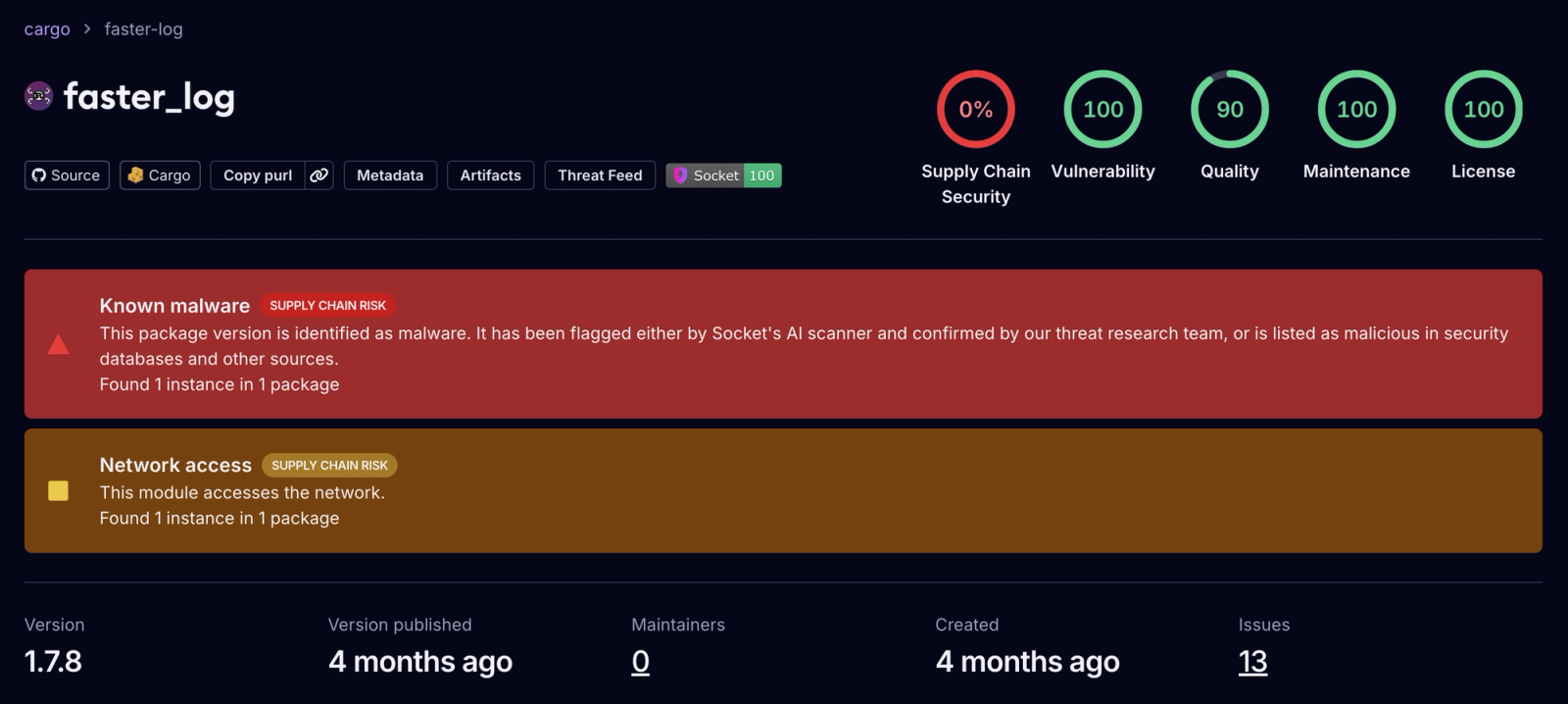
The impostor crates include legitimate-looking logging functionality to evade detection, while a hidden routine scans source files for wallet keys and exfiltrates them to a hardcoded command-and-control (C2) endpoint. Between them, the two crates accumulated 8,424 downloads before being removed from crates.io.
On May 25, 2025, the threat actors uploaded faster_log version 1.7.8 and async_println version 1.0.1 to crates.io, copying the README, repository links, and naming conventions of the genuine fast_log package.
Socket’s Threat Research Team identified two counterfeit packages—faster_log and async_println—published under the aliases rustguruman and dumbnbased.
Socket’s AI Scanner flagged faster_log as known malware after detecting typosquatting indicators and the presence of exfiltration code.
Copyright of this story solely belongs to gbhackers . To see the full text click HERE



