Fileless Remcos Attacks: Injecting Malicious Code into RMClient to Evade EDR
gbhackersCyberProof researchers detected a significant surge in Remcos (Remote Control & Surveillance Software) campaigns throughout September and October 2025, exploiting sophisticated fileless techniques to evade endpoint detection and response (EDR) solutions.
By leveraging highly obfuscated PowerShell scripts and process hollowing into Microsoft’s RMClient.exe, attackers are gaining stealthy persistence and targeting browser credentials.
Although Remcos is advertised as a legitimate commercial remote access tool for surveillance and penetration testing, threat actors continue to repurpose it for illicit operations.
The recipient, enticed by a credible “inquiry order” theme, downloaded the file via Microsoft Edge. Once extracted, the archive dropped a batch file under the user’s Temp directory with a path resembling:
C:\Users
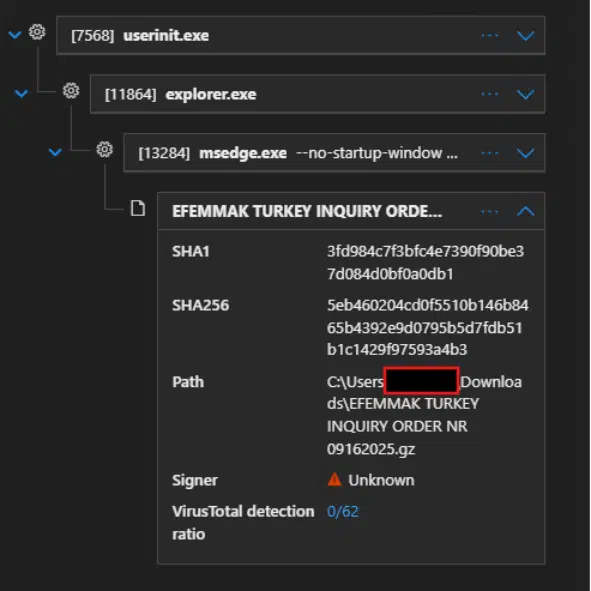
This batch file launched an obfuscated PowerShell script using functions dubbed ‘Lotusblo’ and ...
Copyright of this story solely belongs to gbhackers . To see the full text click HERE



